What are the Five Pillars of Cybersecurity?
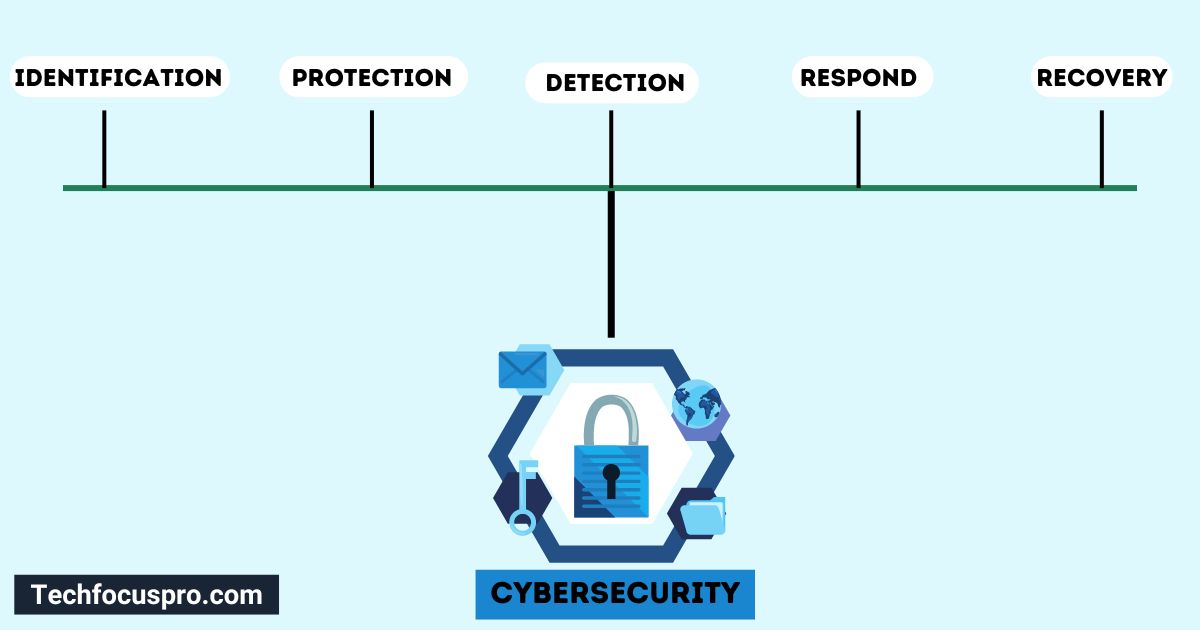
The “Five Pillars of Cybersecurity” are essential concepts that form the foundation of any complete cybersecurity plan.
These pillars guide governments in developing and upholding secure systems, protecting sensitive info from evolving threats, and confirming data integrity, privacy, and availability. Together, they create a robust framework for navigating the complex landscape of modern cyber threats and protecting digital assets.
1: Identification
Inventory of Assets:
The “Identify” aspect of the Five Pillars of Cybersecurity focuses on a vital initial step: recognizing and understanding the various resources within a group that require protection from potential cyber threats.
This includes making a complete Inventory of Assets, where every piece of hardware, software, and data from the most basic physical devices to multiple databases is cataloged. Meaningful what you have is the first step in protecting it.
Risk Assessment:
Risk Assessment goes hand in hand with inventorying assets. It’s about precisely calculating the threats and weaknesses that each asset might face.
This process is vital for ordering cybersecurity efforts based on the level of risk to dissimilar assets. Risks can be anything from data breaches and malware attacks to physical theft or harm.
Management Support:
Equally important is gaining Management Support. This pillar highlights the need for a government’s leadership to actively back cybersecurity events.
Their commitment is vital for allocating the essential resources, time, budget, and workers to uphold and improve cybersecurity defenses. With this support, even the most well-planned cybersecurity plans can stay strong.
2: Protection

The Protect pillar, a core constituent of the Five Pillars of Cybersecurity, focuses on finding robust barriers to deter cyber threats from penetrating an organization’s critical infrastructure. It joins complete strategies to confirm stringent access control, safeguard data honesty, and foster cybersecurity mindfulness across all workforce levels. This active stance is crucial in forestalling security breaches and minimizing potential risks, reflecting the overarching ethos of the Five Pillars of Cybersecurity in creating a resilient and secure digital environment for governments.
Access Control
- What It Means: Entrée Control is a digital gatekeeper. It confirms that only those official persons can view or use certain pieces of info or systems.
- How It Works: This is done through keys, biometric scans, and admission cards. It’s like having a lock on your data and only generous keys to those who need it.
- Why It’s Important: By regulating who gets in, you meaningfully lower the risk of data being stolen or misused by somebody inside or outside your group.
Data Security
- Basics Explained: Data Security is the art of keeping your data safe from unlawful access and confirming that it stays correct and reliable (privacy, integrity, and obtainability).
- Techniques Involved: This can include encryption, creating secure backups, and confirming that data can’t be changed without proper approval.
- Significance: It’s about confirming your data is there when wanted and in the form you expect, without any unwanted surprises from hackers or even chance mishaps.
Awareness Training
- Overview: Mindfulness Preparation is tied to guaranteeing that everybody in your association, starting from the top, knows the dangers of digital dangers and how to stay away from them.
- Key Elements: This could be regular training sessions, emails with tips on spotting phishing scams, and guidelines on safe online behavior.
- Purpose: It’s about making a culture of cybersecurity. When everybody knows what to look for, your group becomes a much harder target for cybercriminals.
By directing these three areas within the Protect pillar, governments can build a strong defense that stops attacks and ensures that any potential breach has minimal impact. This approach is critical for upholding trust and securing the digital scenery of a business in the face of developing cyber threats.
3: Detection

The Detect phase is a vital aspect of the Five Pillars of Cybersecurity. It’s all about having the tools and systems to notice something’s wrong. Think of it as the cybersecurity equal of a smoke alarm in your house. Just as the smoke alarm alerts you to possible fire, the Detect phase alerts administrations to potential cyber threats.
Monitoring Tools
Nursing Tools are the alert eyes that scan the digital environment of an organization 24/7. They are specialized software that looks for uncommon behavior or signs that someone might be trying to break into your systems. It’s like having a safety camera that monitors your digital doorstep, ensuring no unwanted visitors enter.
Anomaly Detection
Oddity Identification is a piece like an analyst working behind the scenes. It realizes what ‘typical’ resembles for your organization. Afterward, if it sees anything odd (like a client signing in at 3 AM, the point at which they ordinarily sign in at 9 AM), it raises a banner. This is urgent because it can get issues that could not be network safety dangers immediately but could show something more evil is in progress.
Incident Reporting
Finally, Incident Reporting ensures it’s not just shrugged off when something goes wrong. This is about having a clear plan for what to do when you detect something suspicious. It means someone’s always ready to take action, whether shutting down access to a cooperated account or alerting the establishments. Fast action can differentiate between a minor hiccup and a primary disaster.
Together, these mechanisms of the Detect pillar guarantee that organizations can identify and respond to cyber threats swiftly. This proactive way is vital for reducing the impact of cyber attacks, keeping the organization’s data safe, and upholding the trust of its stakeholders. It’s an essential part of the Five Pillars of Cybersecurity, helping to create a safer digital world for everybody.
4: Respond
The response phase is a severe section of the Five Pillars of Cybersecurity, concentrating on being ready and having a plan of attack for when cybersecurity incidents happen.
Incident Response Plan
Creating an acting strategy, an Incident Response Plan is like having a fire drill procedure – it safeguards everyone knows what to do and where to go when an alert goes off. This plan includes clear roles and tasks, ensuring no mix-up during a crisis. These actions can be taken quickly and professionally.
Communication Plan
A Communication Plan is also essential. It’s the diagram for how to share data during a network safety occurrence, specifying who has to know what and when. Consider it a method for keeping everybody in the know, from your group to clients and accomplices, without causing a frenzy or spreading falsehood.
Analysis and Mitigation
Lastly, the Analysis and Mitigation steps are about looking at the event carefully, figuring out how and why it ensued, and then taking steps to ensure it doesn’t happen again. This involves:
- Carefully reviewing the events.
- Covering the damage to prevent it from dispersal.
- Informing your security events based on what you’ve learned.
Together, these elements confirm that when faced with a cybersecurity threat, governments can respond efficiently, minimize injury, and bounce back as fast and securely as possible. As part of the holistic approach of the Five Pillars of Cybersecurity, the response phase is crucial for upholding honesty and trust in an organization’s digital environment.
5: Recovery
The recovery phase forms a vital pillar of the Five Pillars of Cybersecurity, highlighting flexibility and learning after a cyber incident. It focuses on the plans and actions needed to return to standard processes, reinforce security posture, and safeguard continuous working capability through and after a cybersecurity event.
Recovery Plans
Recovery Plans are complete roadmaps designed to guide organizations through restoring services and data cooperated during a safety breach. These plans include specific steps for system repairs, data recovery, and renovating regular services, reducing downtime and operational impact. By prudently predefining these actions, organizations ensure a swift and effective return to normalcy, which is vital for upholding stakeholder trust and operational honesty.
Lessons Learned
The Lessons Learned process is essential to recovering from a cybersecurity event. This involves thoroughly reviewing and studying the event and the organization’s response. Organizations can improve their cybersecurity measures, policies, and response strategies by classifying what was done well and where improvements are needed. This continuous learning and adaptation process fortifies the organization’s fortifications against future threats, exemplifying the lively nature of cybersecurity.
Continuity Planning
Continuity Planning is vital for confirming that an organization can uphold core functions in the instant response to a cyber incident and throughout the recovery process. This design includes classifying serious operations, resources, and events that ensure the organization can continue to operate under adverse conditions. Effective continuity plans reduce the risk of essential service interruptions and monetary losses, underpinning the flexibility of the organization’s infrastructure.
In conclusion, the Recover phase of the Five Pillars of Cybersecurity highlights the importance of readiness, flexibility, and ongoing development in the face of cybersecurity threats. It confirms that administrations can not only bounce back from incidents but also emerge more potent and secure, ready to face future challenges in the numerical landscape.