Mobile App Security Best Practices for Developers

Strong security measures are essential in the ever-changing world of mobile app development. When it comes to protecting their applications, Saudi Arabian developers encounter certain difficulties and possibilities.
Mobile applications make everyday activities such as communication, commerce, entertainment, and healthcare possible. However, when people rely more on mobile apps, there’s a greater chance of security lapses and vulnerabilities.
Developers must prioritize security throughout the app development process to preserve customer confidence and safeguard sensitive user data.
Importance of Mobile App Security
One cannot emphasize how important mobile app security is. A single security breach can result in significant financial losses, harm to one’s reputation, and legal implications. Preserving the security of mobile applications is crucial in Saudi Arabia because mobile usage is pervasive in a number of sectors, including government services, healthcare, and banking.
To safeguard against ever-evolving dangers like malware, data breaches, and unauthorized access, developers must incorporate strong security measures in tandem with their efforts to exceed user expectations for functionality and usability. By implementing best practices in security, mobile app developers may reduce risks and increase user confidence.
Keep checking back as we explore more in-depth recommended practices for Saudi Arabian mobile application security. The sections that follow will cover key tactics for implementing safe authentication systems, protecting data transmission, conducting frequent security audits, and other related tasks.
Understanding the Threat Landscape

Developers of mobile applications in Saudi Arabia need to be aware of the various risks that target their apps. Data breaches, viruses, illegal access, and other dangers are among them.
As per Forbes:
In 2018, mobile malware attacks and mobile account takeovers nearly doubled.
Cybercriminals’ methods for exploiting weaknesses in mobile apps are changing along with the digital ecosystem. It is imperative to comprehend these dangers to effectively implement security measures that safeguard user data and the application’s integrity.
Types of Mobile App Security Threats
| Threat Type | Description | Examples/Techniques/Impact |
| Malware Attacks | Malicious software designed to harm or exploit devices. | Viruses, Trojans, Spyware |
| Phishing Attacks | Deceptive methods to acquire sensitive information. | Use of fake emails, websites, or messages to steal user data. |
| Man-in-the-Middle (MITM) Attacks | Interception of communication between two parties. | Attackers insert themselves into the communication chain, often via unsecured networks. |
| Insecure Data Storage | Improperly secured data that is vulnerable to breaches. | Risks of data breaches, unauthorized access to sensitive information. |
| Insufficient Transport Layer Protection | Weak security protocols during data transmission. | Ensures data is encrypted during transfer to prevent interception. |
Best Practices for App Security in KSA
Implementing Secure Authentication Mechanisms
Authentication is essential for securing mobile apps. Developers should use strong authentication techniques, including multi-factor authentication (MFA), to improve security.
Using multiple factors to authenticate identification (password, biometric data, such as fingerprint or facial recognition) or a one-time code given to a mobile device—known as multi-factor multi-factor authentication (MFA)—adds an additional layer of security. In the event that credentials are stolen, this greatly lowers the chance of unwanted access.
Securing Data Transmission
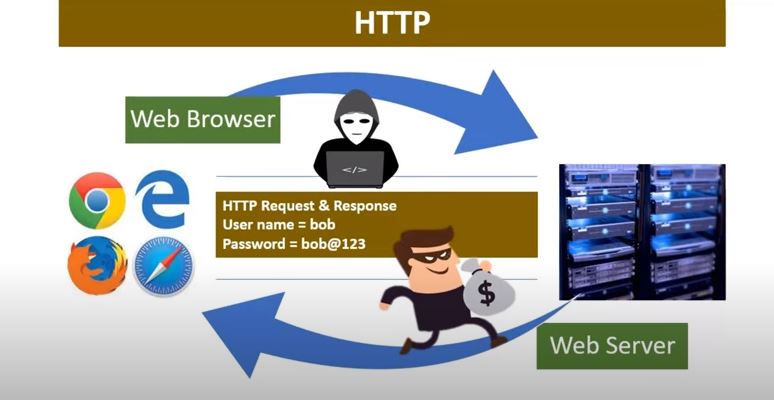
Protecting sensitive data from harmful entities during transmission by encrypting it with protocols such as HTTPS guarantees that it is not intercepted. With HTTPS, data is protected from unauthorized access and manipulation by encrypting the connection between the app’s server and the user’s device.
In particular, when sending sensitive data like login credentials, bank account information, or personal information, HTTPS implementation is crucial.
Regular Security Audits and Penetration Testing
Conducting regular security audits and penetration testing helps identify vulnerabilities in the app’s code and infrastructure, allowing developers to address security weaknesses proactively. Security audits involve comprehensive reviews of the app’s architecture, codebase, and data handling practices to identify potential vulnerabilities or compliance gaps.
Penetration testing, on the other hand, involves simulated attacks to assess the app’s resilience against real-world threats. By identifying and mitigating vulnerabilities early in the development process, developers can enhance the overall security posture of their mobile applications.
Summary of Best Practices
To wrap up, here are the key best practices for mobile app security:

- Avoid Hardcoded Secrets: Never store sensitive information like API keys directly in your code.
- Validate and Sanitize Inputs: Always check the data coming into your app to prevent attacks like SQL injection.
- Use Encryption: Protect sensitive data both when it’s stored and when it’s being transferred.
- Principle of Least Privilege: Give users and processes the minimum level of access necessary.
- Strong Authentication: Implement robust authentication methods, including multi-factor authentication.
- Role-Based Access Control: Limit what different users can do based on their role within the app.
- Secure Session Management: Ensure that sessions are properly secured and managed.
- Secure Data Storage: Safely store data to protect it from unauthorized access.
- Data Encryption: Encrypt data both in transit and at rest to keep it confidential.
- Prevent Data Loss: Implement strategies to avoid accidental or malicious data loss.
- Secure Communication: Use secure protocols like SSL/TLS to ensure data integrity and privacy during transmission.
- Safe API Use: Avoid using insecure APIs and perform regular checks to ensure their security.
- Monitor Network Traffic: Keep an eye on network activity to detect and respond to unusual behavior.
- Protect PII: Ensure personally identifiable information is handled securely.
- Follow Privacy Regulations: Comply with relevant privacy laws like GDPR and CCPA.
- Evaluate Third-Party Integrations: Regularly assess and update third-party libraries and SDKs for security vulnerabilities.
- Regular Security Testing: Perform static and dynamic analysis and penetration testing, as well as use automated scanning tools to detect vulnerabilities.
- Incident Response: Have a plan ready for detecting, responding to, and managing security incidents.
- Educate Developers: Continuously train your development team on security best practices and emerging threats.
Compliance with Regulatory Standards
For legal compliance and user data protection, developers operating in Saudi Arabia are required to abide by both local and international regulatory standards, including GDPR and the country’s data protection legislation.
These laws severely limit the gathering, storage, processing, and security of personal information in mobile applications. By adhering to regulatory regulations, developers lower their legal risks and show that they are committed to protecting user privacy and upholding confidence.
While we are talking about app security Advanced protection Technologies also play a crucial role to enhance security in digital landscape.
Educating Users on Security Practices
The greatest way to improve an app’s overall security posture is to teach users about best practices for security. User activities, such as exchanging credentials, using weak passwords, or falling for phishing scams, are often the cause of security breaches.
For example, developers should incorporate password strength meters, advice on spotting phishing efforts, and notifications to activate security features like biometric authentication into their apps to raise user awareness of security.
Collaborating with Trusted Mobile App Security Experts

Developers can strengthen app security measures with professional advice and specialized tools by collaborating with a respectable Saudi Arabian mobile app security business or app development company . These professionals provide thorough evaluations of security, threat analysis, and customized fixes for vulnerabilities unique to mobile apps.
Developers can stay abreast of developing risks, apply cutting-edge security procedures, and guarantee ongoing enhancements to app security practices by utilizing their experience.
FAQs About Mobile App Security
What are the common security threats faced by mobile apps in Saudi Arabia?
Security risks for mobile apps in Saudi Arabia include phishing efforts, malware assaults, insecure data storage, and compromised credentials. To secure user data and uphold the integrity of the app, developers need to be on the lookout for these dangers and take prompt action.
What is meant by mobile app security?
Mobile app security refers to the practices and measures taken to protect mobile applications from security threats and vulnerabilities. This includes safeguarding user data, preventing unauthorized access, and ensuring secure communication.
What is the best security for a mobile app?
The best security for a mobile app includes a combination of strong data encryption, robust authentication and authorization methods, secure coding practices, regular security testing, and compliance with regulatory standards. Incorporating trusted security libraries and SDKs can also enhance app security.
What are the most common mobile app security threats?
The most common mobile app security threats include malware attacks, phishing attacks, man-in-the-middle (MITM) attacks, insecure data storage, and insufficient transport layer protection.
How can developers protect mobile apps from malware?
Developers can protect mobile apps from malware by implementing robust security measures such as regular security testing, using secure coding practices, and incorporating trusted security libraries and SDKs.
How important is developer education in maintaining mobile app security?
Developer education is crucial. Providing ongoing training about emerging threats, security best practices, and secure coding techniques fosters a security-first mindset. It equips developers to build more secure applications.
What are some key regulatory standards for mobile app security?
Key regulatory standards for mobile app security include:
- The General Data Protection Regulation (GDPR).
- California Consumer Privacy Act (CCPA).
- Health Insurance Portability and Accountability Act (HIPAA).
Compliance with these regulations is essential to protect user data and avoid legal penalties.
Conclusion
Ensure the security of your apps in mobile app development in Saudi Arabia.. In this tutorial, we’ve covered key best practices that developers may apply to strengthen the security of their mobile apps and safeguard sensitive user information.
App developers must be proactive in in-app security, identifying and mitigating various security risks, implementing robust authentication procedures, and adhering to regulatory guidelines.
Developers may lower the risks of malware, illegal access, and data breaches by having a security-focused approach from the beginning and continuing throughout the lifecycle of the app.